Remote SSH commands require double escaping before hitting the DefaultShell · Issue #1082 · PowerShell/Win32-OpenSSH · GitHub

Roughly 2,500 beds at the disposal of the Czech State Material Reserves Administration (SSHR) will be used to increase hospital capacity and create a reserve capacity due to the coronavirus crisis, Central




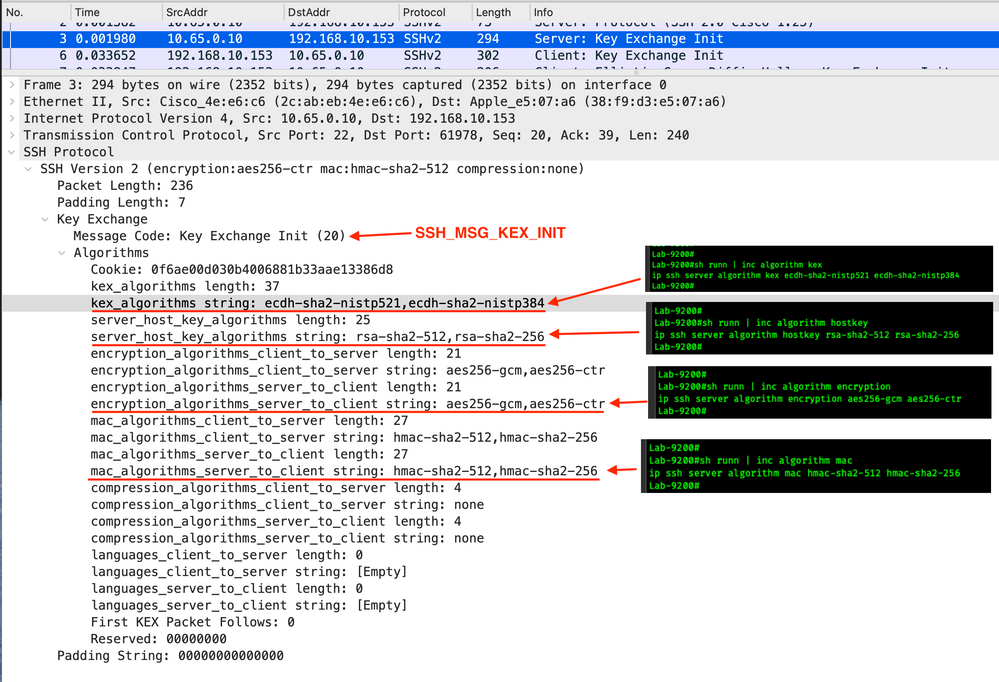
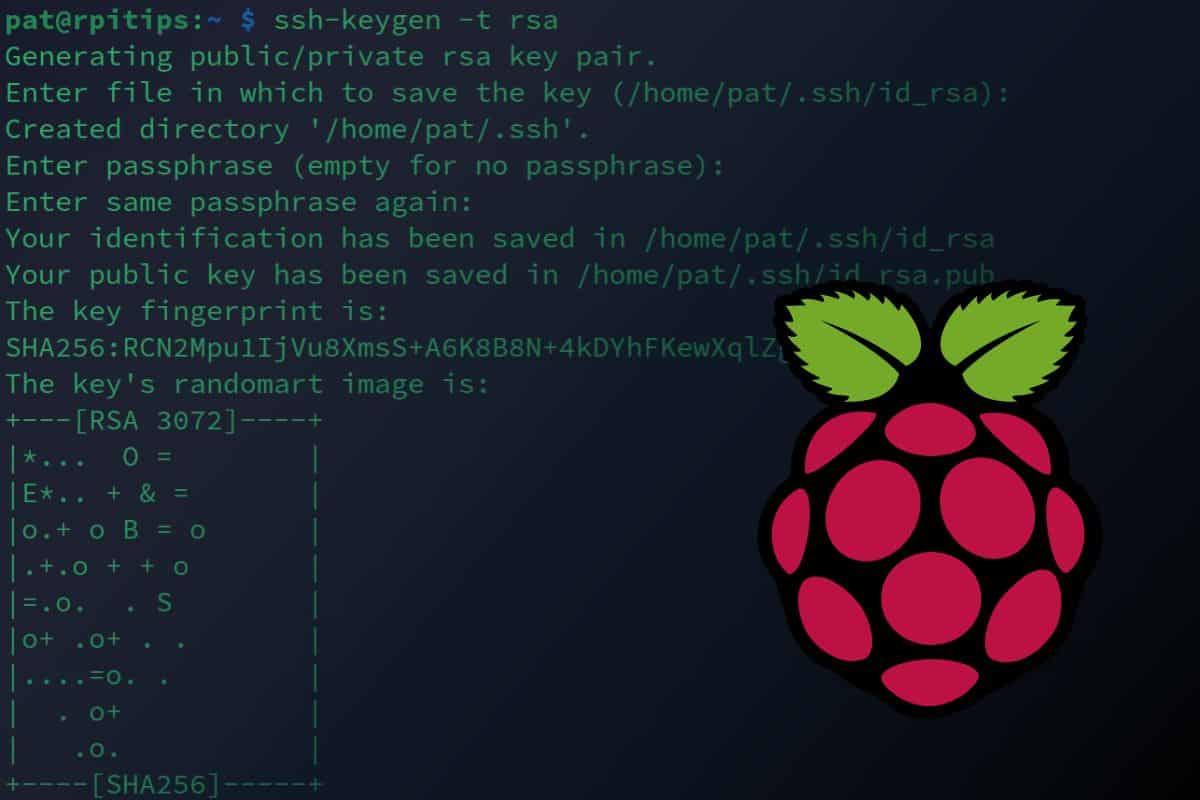
![How to Set up SSH Client and Server on Windows 10 [Full Guide] - MiniTool Partition Wizard How to Set up SSH Client and Server on Windows 10 [Full Guide] - MiniTool Partition Wizard](https://www.partitionwizard.com/images/uploads/2020/04/ssh-client-win10-thumbnail.jpg)